Tips on Identifying Spoofed Emails
More likely than not, you’ve been a target of email spoofing at least once in your life. That’s because email spoofing targets everyone, and scammers are becoming more deceitful every day. Email spoofing is the act of sending emails with a forged sender address. It tricks the recipient into thinking that someone they know or trust sent them the email. Usually, it’s a tool of a phishing attack, designed to take over your online accounts, send malware, or steal funds.
Many spoofed emails can be difficult to detect; however, there are several tips you can use to help identify spoofed emails.
First, carefully look at the email to identify irregularities. While one error may not constitute a spoofed email, observing multiple errors should raise additional caution requiring further research.
Common “Red flags” include:
-
- An unfamiliar greeting
- Irregular time and format
- Poor grammar and spelling
- Sense of urgency
- Suspicious attachments
- Unusual requests
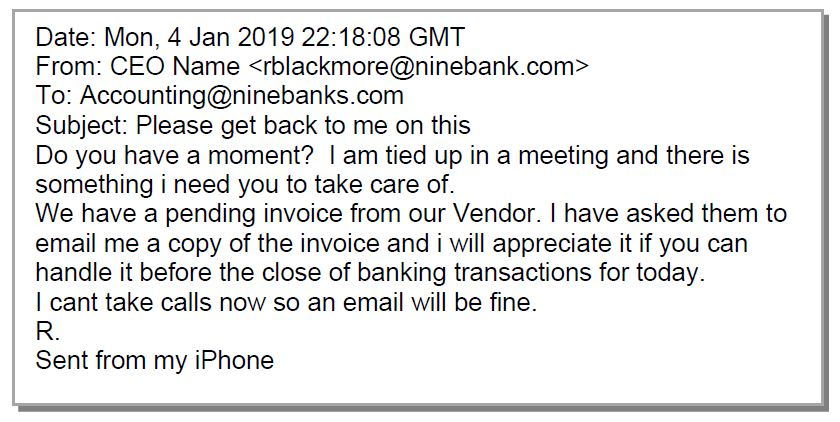
The example of a phishing email shown in Figure 2 reveals several “red flags” which can alert the reader if they stop, think and then click.
Follow-up emails by Business Email Compromise scammers are designed to be authoritative and provide instructions for performing the wire transfer.
- Many of the same irregularities appear on subsequent emails.
- In this example, the wire transfer comes at timeframe inconsistent with where your offices are located or where your CEO may be.
- An attachment is also included in the email. Opening attachments on emails such as this can be a mistake as it may contain malicious code.
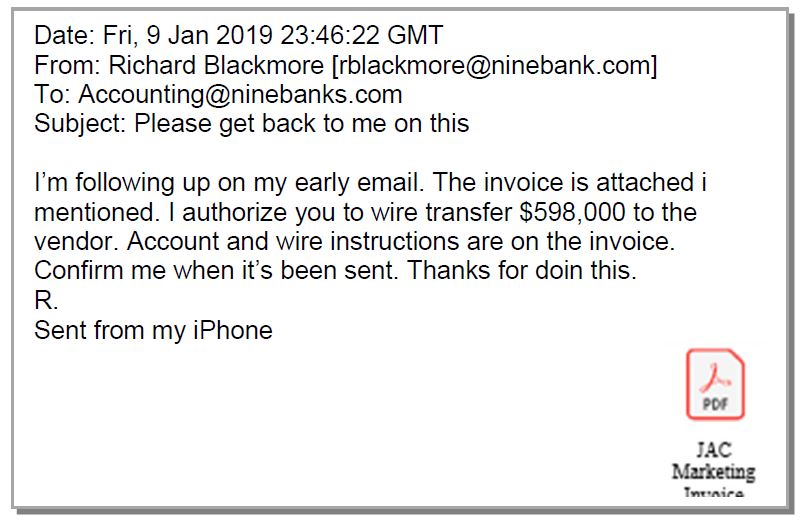
Figure 3. Example of spoofed email requesting the wire transfer.
How to Protect Your Business
- Back up your data - Regularly back up your data and make sure those backups are not connected to the network. That way, if a phishing attack happens and hackers get to your network, you can restore your data. Make data backup part of your routine business operations.
- Keep all security up to date - Always install the latest patches and updates. Look for additional means of protection, like email authentication and intrusion prevention software, and set them to update automatically on your computers. On mobile devices, you may have to do it manually.
- Alert your staff - Share with them this information. Keep in mind that phishing scammers change their tactics often, so make sure you include tips for spotting the latest phishing schemes in your regular training.
- Deploy a safety net - Use email authentication technology to help prevent phishing emails from reaching your company’s inboxes in the first place.
What to Do If You Fall for a Phishing Scheme
- Alert others - Talk to your colleagues and share your experience. Phishing attacks often happen to more than one person in a company.
- Limit the damage - Immediately change any compromised passwords and disconnect from the network any computer or device that’s infected with malware.
- Follow your company’s procedures - These may include notifying specific people in your organization or contractors that help you with IT.
- Notify customers - If your data or personal information was compromised, make sure you notify the affected parties ? they could be at risk of identity theft. Find information on how to do that at Data Breach Response: A Guide for Business.
- Report it - Forward phishing emails to [email protected] (an address used by the Anti-Phishing Working Group, which includes ISPs, security vendors, financial institutions, and law enforcement agencies). Let the company or person that was impersonated know about the phishing scheme. And report it to the FTC at FTC.gov/Complaint.


